基于MIN高安可的VPN系统Highly secure and available VPN system based on MIN
一、系统整体功能介绍
1. Introduction to the overall function of the system
Based on the self-developed co-management and multi-identity MIN network system, Foshan Saisichan Technology Co., Ltd. has developed a MIN-VPN mobile high-security private network system, which supports the coexistence of various identities such as identity, content, service, IP address, BeiDou, etc. , integrates a variety of security management and control technologies to meet the practical needs of users such as mobile office, identity management, rights management, log storage, behavior detection, identity authentication, and network security. MIN-VPN's small, medium and multi-level application scenarios include government, military, radio and television, finance, electric power and other large enterprises or key industry private networks with high security requirements, industrial Internet and vehicle networking scenarios that require unified identification services.
MIN-VPN移动高安可专网系统通过多项技术实现网络高效访问和有序监管。采用区块链技术的日志记录,实现了可信记录;依靠拟态防御技术保障核心系统的内生安全;基于人工智能技术的用户行为检测和安全态势感知系统,保障了网络和信息安全。结合真实身份和生物特征的身份管理方案,确保用户识别的可靠性和用户管理的有效性;将数据包与用户信息高度绑定,实现数据和行为可追溯;结合多种密码学签名技术,达到隐私保护与可管可控的平衡。
MIN-VPN mobile high security private network system realizes efficient network access and orderly supervision through a number of technologies. The log records of blockchain technology are used to achieve credible records; the endogenous security of the core system is guaranteed by the mimic defense technology; the user behavior detection and security situational awareness system based on artificial intelligence technology ensures network and information security. The identity management scheme that combines real identity and biometric features ensures the reliability of user identification and the effectiveness of user management; highly binds data packets with user information to achieve data and behavior traceability; combines a variety of cryptographic signature technologies to achieve the balance between privacy protection and manageability.
二、主要技术方案
2. Main technical solutions
1 建设方案
1 Construction plan
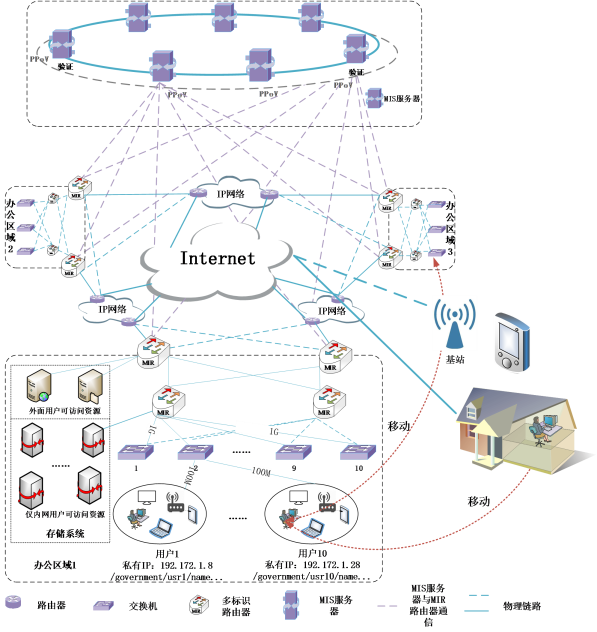
图1 MIN网络初步建设方案
MIN网络可跨公司、跨地点部署,测试环境如图1所示。该拓扑由交换机、多标识路由器(MIR)、MIS服务器等设备为主构成,这些设备均处于MIN网络环境中。在两个地点出口处分别部署两台多标识路由器MIR(共4台),在这4台服务器上部署MIS系统的区块链节点,组成该网络的标识管理系统。同时该4台MIR也是各个地方访问IP网络的出口。
The MIN network can be deployed across companies and locations, and the test environment is shown in Figure 1. The topology consists mainly of switches, multi-identifier routers (MIRs), MIS servers, and other devices, which are all in the MIN network environment. Two Multi-Identifier Routers MIRs (4 in total) are deployed at the exit of each of the two locations, and the blockchain nodes of the MIS system are deployed on these 4 servers to form the identifier management system of this network. The four MIRs are also the egress points for each location to access the IP network.
两个地点内部使用多标识路由器组成MIN专网,多标识路由器之间直接使用网线连接,直接使用链路层协议传输MIN网络分组,而不使用IP网络通信协议。两个地点的多标识路由器使用IP外网作为通信隧道,即使用IP隧道交换多标识网络分组,使两个单独的专网之间在逻辑上形成统一的MIN网络。
Within the two locations, a private MIN network is formed using multi-identifier routers, which are directly connected to each other using network cables and transmitting MIN network packets directly using link layer protocols, instead of using IP network communication protocols. The multi-identifier routers at the two locations use IP extranets as communication tunnels, i.e., they use IP tunnels to exchange multi-identifier network packets, so that a unified MIN network is logically formed between the two separate private networks.
在多标识网络内部需要保留有一定的私有IP地址,私有IP地址主要用于网络边缘用户接入。在未来的场景中,用户可以使用支持多标识网络协议的小型家用路由器作为用户的接入设备,以实现完全的去IP化。
A certain number of private IP addresses need to be reserved inside the multi-identifier network, and the private IP addresses are mainly used for user access at the network edge. In future scenarios, users can use small home routers that support the multi-identifier network protocol as user access devices to achieve complete de-IPing.
2 功能介绍
2 Function introduction
1. 支持渐进式去IP:MIN网络与IP网络兼容,可以直接部署在IP网络上,现有的应用层软件无需更改,借助MIN客户端即可完成网络协议的转换。
2. 移动办公:可以让办公人员摆脱时间和空间的束缚、提高工作效率、加强远程协作, 无论在外出差,还是正在上班的路上,外网用户都可以及时审批公文、浏览公告、处理个人事务、访问内网资源等等。
3. 身份管理:身份管理包括用户注册、用户登录和证书下发。用户在注册过程中需进行实名制,向系统提供真实姓名、身份证号、手机号码、指纹信息、人脸特征、设备公钥等信息。MIS收到用户登录信息并验证通过后将该用户的证书下发至边界MIR用于路由转发阶段的身份认证。
4. 权限管理:权限管理指的是根据系统设置的安全规则或者安全策略,用户可以访问而且只能访问自己被授权的资源,不能非法访问未授权资源,系统通过“鉴权”识别“越权”行为,保障内网资源的安全。用“规则”一词表示资源,规则可以授权给用户,管理员负责分配规则,管理员分为高级管理员和普通管理员,其权限如下表所示。
|
|
规则的使用权 |
创建 |
指派给普通管理员 |
编辑 |
给用户或者用户组关联指派 |
|
高级管理员 |
支持 | 支持 | 支持 |
支持 |
支持 |
|
普通管理员 |
创建或被授权后支持 |
支持 | 支持 | 不支持 | 支持 |
5. 日志存储:MIN服务端会提取每个数据包的目的地址、目的端口、HTTP URL等信息,与用户身份信息结合形成用户访问记录,然后发送给MIS。
6. 行为检测:系统应对合法用户的身份和行为进行有效管理,具有检测和识别合法用户非法行为的能力。MIS的行为检测功能会根据需求和规则,对用户的访问记录进行分析和审查。
7. 内生安全:多重签名机制实现网络分组的可溯源,包括用户签名和首跳路由器签名。MIN路由器中的所有路由器都可以通过签名验证网络分组的合法性,对于不合法数组分组可以追溯到个人和用户接入地点。
8. 态势感知:安全态势感知系统能够实现双栈网络的实时监测和目标主机的安全检测,并且对当前系统的整体安全进行实时评估和预测。
9. 抵抗传统IP攻击:MIN网络体系采用与现有IP网络完全不同的数据传输方式,使得很多IP体系下的攻击手段对MIN网络无效。如IP网络下的ARP攻击、DNS劫持、端口嗅探、漏洞扫描、RAT(远程控制连接)型木马攻击等攻击,经过测试,都无法在MIN专网环境下发挥作用。
1. Support progressive de-IP: MIN network is compatible with IP network and can be directly deployed on IP network. The existing application layer software does not need to be changed, and the network protocol conversion can be completed with the help of MIN client.
2. Mobile office: It can free office staff from the constraints of time and space, improve work efficiency, and strengthen remote collaboration. Whether on business trips or on the way to work, extranet users can promptly approve official documents, browse announcements, handle personal affairs, and access internal Internet resources, etc.
3. Identity management: Identity management includes user registration, user login and certificate issuance. During the registration process, users need to implement a real-name system and provide the system with information such as their real name, ID number, mobile phone number, fingerprint information, facial features, and device public key. After the MIS receives the user's login information and passes the verification, the user's certificate is issued to the border MIR for identity authentication in the routing and forwarding phase.
4. Rights management: Rights management refers to that according to the security rules or security policies set by the system, users can access and only access their authorized resources, and cannot illegally access unauthorized resources. Ensure the security of intranet resources. The word "rule" is used to represent resources. Rules can be authorized to users. Administrators are responsible for assigning rules. Administrators are divided into senior administrators and ordinary administrators. The permissions are shown in the following table.
|
|
Right to use the Rules |
Create |
Assigned to a normal administrator |
Edit |
Assign a user or user group association |
|
Senior Administrator |
Support |
Support |
Support |
Support |
Support |
|
Normal Administrator |
Post-creation or post-authorization support |
Support |
Support |
Not support |
Support |
5. Log storage: The MIN server will extract the destination address, destination port, HTTP URL and other information of each data packet, combine with the user identity information to form a user access record, and then send it to MIS.
6. Behavior detection: The system should effectively manage the identities and behaviors of legitimate users, and has the ability to detect and identify illegal behaviors of legitimate users. The behavior detection function of MIS will analyze and review users' access records according to requirements and rules.
7. Endogenous security: The multi-signature mechanism realizes the traceability of network packets, including user signatures and first-hop router signatures. All routers in the MIN router can verify the legitimacy of network packets through signatures, and the illegal array packets can be traced back to individuals and user access locations.
8. Situational awareness: The security situational awareness system can realize the real-time monitoring of the dual-stack network and the security detection of the target host, and conduct real-time assessment and prediction of the overall security of the current system.
9. Resistance to traditional IP attacks: The MIN network system adopts a completely different data transmission method from the existing IP network, making many attack methods under the IP system ineffective against the MIN network. Attacks such as ARP attacks, DNS hijacking, port sniffing, vulnerability scanning, and RAT (remote control connection) Trojan horse attacks under the IP network have been tested and cannot be used in the MIN private network environment.
